Digital footprints are the trails of data users leave behind as they move through the online world. These traces can include everything from email activity and IP addresses to browser settings and device metadata. Every digital interaction helps shape a virtual profile that evolves over time.
Unlike static identifiers like government-issued IDs, digital footprints are dynamic and constantly changing. They reflect real-time behaviors, offering a more nuanced view of a person’s digital identity.
Digital footprints typically fall into two main categories:
- Active footprints: Information users intentionally share—such as social media posts, online reviews, or profile details.
- Passive footprints: Data collected automatically without direct user input—like cookies, location metadata, or IP logs.
These footprints can also be interpreted as behavioral signals:
- Positive signals: Presence on reputable platforms, consistent device usage, or long-standing email addresses.
- Negative signals: Use of burner phones, VPNs, irregular browsing patterns, or a lack of online presence.
In areas like fraud prevention and credit scoring, digital footprints serve as valuable behavioral and contextual indicators. They help fill in gaps where traditional data is limited or missing, improving the accuracy and reliability of decision-making.
How Do Digital Footprints Work?
Digital footprints are far more than just traces left behind by online activity—they are dynamic, evolving representations of a person’s identity, behavior, and interactions across the digital landscape. To understand how they work, we need to look at the vast range of data they comprise and the way these individual data points interact with each other. Each element of a digital footprint offers a unique, often indispensable piece to the puzzle of understanding user behavior, authenticity, and potential risks.
When analyzed holistically, digital footprints can reveal critical insights into a user’s trustworthiness, alert you to fraudulent behavior, and even help predict future actions. These digital markers can be used across industries to safeguard against financial fraud, secure personal and sensitive data, and improve customer service. However, extracting meaningful insights from these signals requires a robust analysis of multiple data sources in context.
The Components of a Digital Footprint
Every digital footprint is built from several key data points. Let's dive deeper into how each of these pieces contributes to building a comprehensive digital profile:
Email Signals
Email addresses are often one of the first pieces of data analyzed when assessing a user's digital footprint. Email history can reveal a wealth of information: it can indicate whether the address has appeared in known data breaches, whether it’s tied to a disposable domain or a reputable one, and even if it's linked to social media or professional profiles. A thorough analysis can also detect whether the email has been associated with suspicious or malicious activity.
- Old vs. New Emails: Older, well-established email addresses tend to be more trustworthy. These accounts often have a verifiable history, may show ties to genuine social media profiles, and are less likely to be disposable.
- Disposable Emails: On the other hand, new or anonymous email addresses, often created using temporary email services, may raise red flags. These are commonly used in fraudulent activities, such as account creation for scams or synthetic identity generation.
Phone Signals
Phone numbers are another critical component in identifying and validating users. Much like email, phone numbers carry valuable metadata that can offer insights into the user's identity, trust level, and risk factors. The country of origin, mobile carrier, and whether the number is linked to a VoIP service or a prepaid plan can help detect potentially fraudulent activity.
- Prepaid vs. Postpaid: Prepaid phones, which are often untraceable and disposable, are typically flagged in fraud prevention systems. In contrast, postpaid numbers, which require a credit check and longer-term commitment, are seen as more stable indicators of a legitimate user.
- Geolocation Mismatches: If a phone number’s geographical location does not align with the user's claimed location or other data points, it could indicate fraudulent behavior, such as location spoofing.
IP Data
IP addresses provide deep insights into where and how a user connects to the internet. IP geolocation helps map out the user's physical location at the time of login. A user claiming to be in one country but logging in from a completely different region might be masking their true location.
- Suspicious IP Patterns: Patterns of behavior, like multiple login attempts from various countries or proxies, can be flagged as signs of fraud or unauthorized access.
- Consistency: If a user consistently logs in from the same IP range or a consistent geographic area, it can reinforce the legitimacy of the account. However, inconsistent or fluctuating IP addresses may suggest an effort to evade detection.
Device Data
The data collected from the devices a user uses can help reinforce their identity and behaviors. Device metadata includes technical identifiers like operating systems, screen resolutions, device types, and timezones. These data points are not just useful for tracking activity but also for identifying fraudulent behavior.
- Device Fingerprinting: By analyzing patterns in device data, such as screen resolution or browser type, fraud detection systems can develop a “fingerprint” for each device. If a user typically logs in from a particular device, but suddenly their session originates from a different device or operating system, it could be a sign of a potential breach or a fraud attempt.
- Automation Detection: Changes in device data, such as the use of emulators or automation tools (which can manipulate device data), can be an indicator of bots attempting to mimic human behavior. Detecting such inconsistencies helps organizations flag fraudulent activities early.
Social Media and Digital Presence
Social media profiles provide rich context and can significantly bolster the credibility of a digital footprint. Profiles on professional platforms like LinkedIn or GitHub, or social platforms such as Facebook, Twitter, or Instagram, can all help establish the authenticity of a user.
- Long-Term Engagement: Users with consistent, long-term activity across different platforms—whether it’s posting, commenting, or connecting with others—are often easier to verify. These profiles usually have more robust digital histories and verifiable connections.
- Lack of Presence: Conversely, an absence of any social media activity, especially when combined with other irregular digital signals, can raise suspicions. Synthetic identities often lack a genuine social presence, which can be a key indicator of fraud.
Breach Exposure
Interestingly, being linked to past data breaches can sometimes add credibility to a user’s digital footprint. While this may seem counterintuitive, it’s important to note that real, long-term users of the internet are more likely to have their information exposed in data breaches over time.
- Historical Data Breaches: A user with no prior exposure to breaches could indicate a fabricated identity, especially when all other digital signals appear to be “too clean” or artificially constructed.
- Dark Web Scraping: Fraud detection systems often scan public leak databases and dark web dumps to check if user information has been exposed. An account that has been exposed to past breaches may seem more legitimate than one that has no history of data exposure.
Digital Footprints for Fraud Prevention
Traditionally, fraud detection has relied on static identifiers like government-issued IDs, credit reports, and password authentication. While these methods form the backbone of identity verification, they often fall short in keeping up with the rapid evolution of fraud tactics—ranging from account takeovers and identity theft to synthetic identities and refund abuse.
A Dynamic Defense Strategy
Digital footprint analysis introduces a more adaptive, real-time approach to fraud prevention. Rather than depending solely on fixed data points, it evaluates behavioral patterns and technical signals behind every user interaction—surfacing subtle inconsistencies that static systems may overlook.
For instance, if a user’s stated location doesn’t align with their IP geolocation, it could be a sign of an account takeover. A sudden flurry of device changes tied to the same account may suggest session hijacking or bot activity. Similarly, the absence of a digital presence—such as no social media footprint or breach history—can indicate a synthetic identity, a common tactic in organized fraud rings.
Reducing False Positives, Increasing Trust
Unlike rigid rules-based systems that often generate false positives and frustrate legitimate users, digital footprinting introduces context-aware intelligence. It learns from evolving user behaviors, assesses risk in real time, and adapts dynamically to the context of each session. As a result, trustworthy users can pass through with minimal friction, while high-risk interactions are flagged for deeper scrutiny.
This behavior-first approach significantly reduces disruptions for honest customers while tightening defenses around fraudsters—especially those using emulators, VPNs, or disposable credentials.
Real-World Impact and Trends
Digital fraud continues to grow in scale and complexity across industries. In the UK alone, £1.17 billion was lost to fraud in 2023, affecting sectors from personal finance to eCommerce and fintech. Globally, nearly half of online merchants in 2024 identified refund or policy abuse as their most pressing fraud challenge. Another 45% reported facing first-party misuse, often known as “friendly fraud,” where customers falsely dispute legitimate purchases (Source: Statista).
Unlike transactional frauds such as phishing or card testing—which can often be caught at the point of sale—these post-purchase attacks are far harder to detect. That’s where behavioral insights and anomalies in digital footprints prove invaluable. They offer a deeper, real-time understanding of user intent—helping organizations combat not just the fraud they can see, but the fraud they never would have caught with static data alone.
Digital Footprints Analysis Across Industries
Digital footprint analysis is revolutionizing how industries combat fraud and assess risk by leveraging a broad spectrum of behavioral and contextual signals—from device data and IP addresses to social media presence and digital reputations.
eCommerce
The eCommerce industry faces a unique challenge in balancing seamless customer experiences with the necessity of preventing fraud, particularly from first-time fraudsters. Fraudsters often employ tactics such as using disposable email addresses, virtual phone numbers, and anonymized devices to create fake accounts. To identify these malicious actors early, eCommerce platforms now employ digital footprint analysis, which looks at a broad spectrum of factors.
For example, one of the key signals is the quality of the email domain used. Fraudsters often use free email domains (e.g., Gmail, Yahoo), while legitimate users may have custom or corporate domains. Device consistency is another significant indicator—users who frequently switch devices or use VPNs are more likely to be fraudulent. Additionally, a lack of social media activity or an absence of an online presence is a red flag. A user logging in from an unknown device, with a newly created email address and no digital footprint, is at a much higher risk for fraudulent intent than someone with a long-established, traceable digital identity.
By cross-referencing digital footprints with historical purchase patterns, behavior across sites, and public online reputations, eCommerce companies can prevent fraudulent transactions before they occur, safeguarding both their business and their customers.
Online Lending and Fintech
In the world of online lending and fintech, assessing creditworthiness without access to traditional credit histories is a major challenge. Many applicants lack established credit records, making it difficult to assess their financial reliability using traditional methods. To address this gap, fintech companies are increasingly turning to digital footprint analysis, specifically Open-Source Intelligence (OSINT), which can provide a much more complete picture of an applicant’s behavior and trustworthiness.
By analyzing a user's social media activity, OSINT tools can reveal information such as their professional background (e.g., LinkedIn profiles) or engagement with relevant online communities (e.g., GitHub for developers). These elements can provide critical clues about a user’s identity and reliability. For example, a robust LinkedIn profile with consistent professional experience can bolster confidence in the applicant's identity, while an active GitHub profile can indicate strong technical skills, helping to verify the applicant’s stated qualifications.
Conversely, an incomplete or shallow digital footprint, such as a missing or minimal social media presence, could indicate the use of synthetic identities or an attempt to hide fraudulent activity. In this way, digital footprints help online lenders assess risk more effectively and ensure the security of their lending processes.
Cryptocurrency
In the fast-paced world of cryptocurrency, digital footprint analysis is an essential tool for identifying fraud and preventing money laundering. Unlike traditional financial systems, cryptocurrency transactions often involve anonymity and can be executed across multiple wallets and platforms. To combat this, digital footprint analysis combines traditional device data with public blockchain information and social media signals.
Suspicious activity is often flagged by unusual patterns, such as wallet addresses linked to frequent device changes, use of VPNs, or unusual IP addresses. Additionally, digital footprints can reveal when a wallet has little to no associated online presence or social media activity, which could signal a higher likelihood of fraud or scam involvement. In many cases, individuals involved in cryptocurrency scams or fraud may leave minimal traces of their real-world identities, relying on anonymous wallets and minimal interactions on social media.
Through the combination of behavioral data, device metadata, and blockchain analysis, cryptocurrency platforms can identify high-risk actors and prevent scams, fraudulent transactions, and bot activity before they cause significant harm.
Marketplaces
Peer-to-peer platforms and online marketplaces, such as those that facilitate the buying and selling of goods or services, rely heavily on the trust between buyers and sellers. This trust is often built on the digital footprints of users, who create profiles that are indicative of their reliability. Verified accounts with consistent device usage, long-standing email addresses, and established social media profiles are typically viewed as trustworthy.
However, newly created accounts or profiles with fragmented digital signals—such as an anonymous email address, lack of social media presence, or inconsistent device use—are often red flags. These signals suggest the possibility of scam attempts or fraudulent listings, which can undermine trust in the platform.
In these environments, digital footprint analysis plays a crucial role in identifying reliable users and ensuring that transactions are secure. By analyzing the consistency and authenticity of digital footprints, platforms can build safer, more trustworthy marketplaces.
Insurance
The insurance industry has long struggled with fraud, particularly when it comes to claims and applications. Traditional methods of verifying identity and assessing risk can be time-consuming and prone to error. With the advent of digital footprint analysis, insurers now have access to a more holistic view of applicants, allowing them to detect fraudulent behavior early in the process.
By examining factors such as social media activity, device usage, and breach exposure, insurers can verify identities and flag suspicious claims. For example, if an applicant's digital footprint reveals a history of multiple breached accounts or inconsistent social media activity, it might indicate a higher risk for fraud. Similarly, the use of disposable phone numbers or email addresses can be a telltale sign of fraud.
Combining these insights with traditional risk assessment methods allows insurers to create a more accurate and reliable picture of the applicant's identity and the likelihood of fraudulent behavior.
Across all these sectors, social media analysis and digital presence serve as powerful tools—not only to confirm identity but also to expose fabricated personas. Genuine users tend to have rich, consistent digital histories, complete with real connections, posts, and interactions. Fraudsters, in contrast, often leave shallow or contradictory footprints.
This broader, multi-dimensional approach to digital footprinting enables businesses to make faster, more accurate decisions, enhance the customer experience, and stay one step ahead of increasingly sophisticated fraud schemes.
Scoreplex Approach in Digital Footprint Analysis
Scoreplex revolutionizes fraud prevention by leveraging AI-driven digital footprint analysis to assess risk and verify identities in real time. The platform silently evaluates over 300 open data sources—social media, messaging platforms, the dark web, and technology platforms—to detect fraudulent activity before it reaches critical stages like Know Your Customer (KYC) compliance or credit scoring.
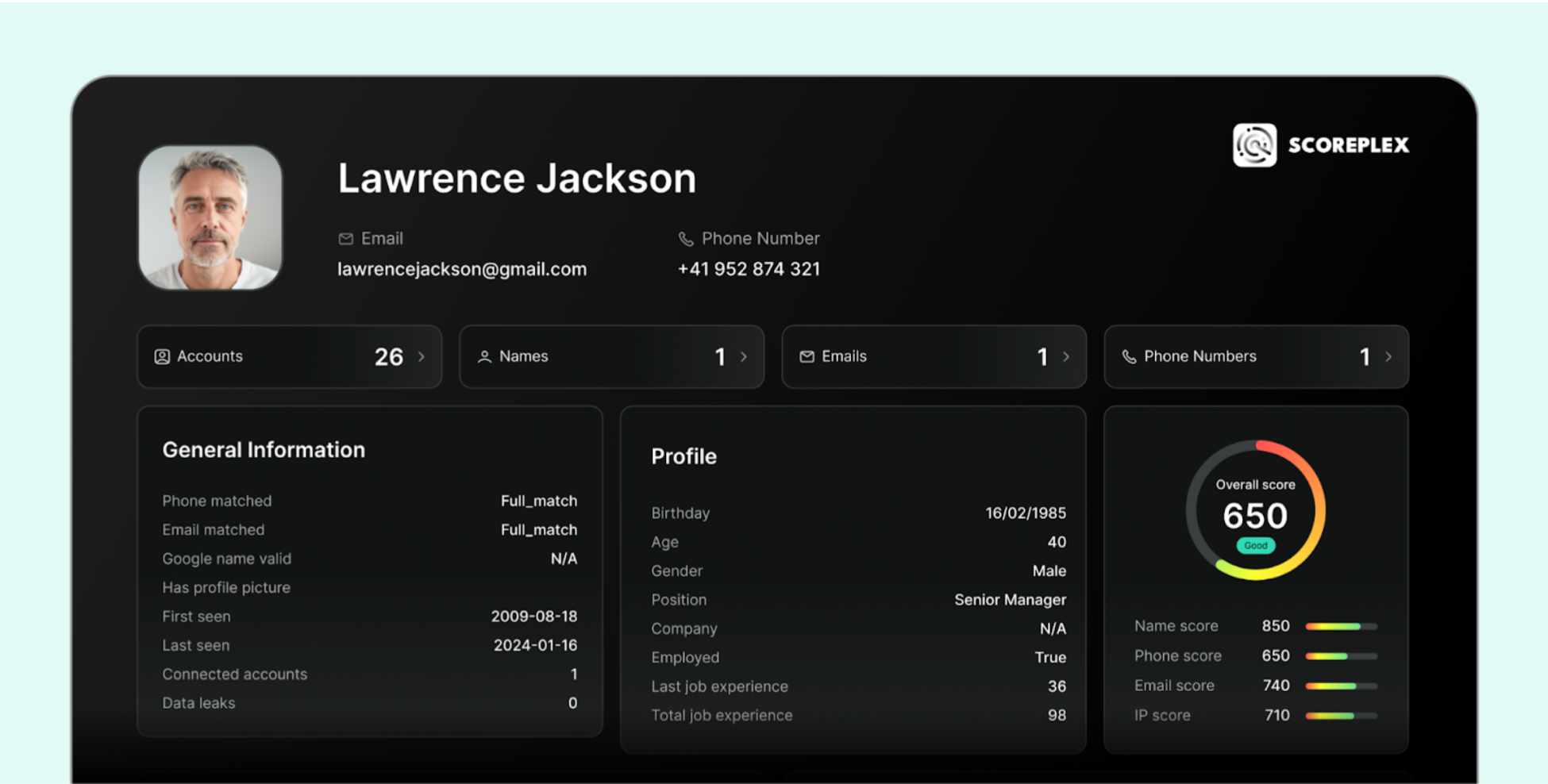
Key Features of Scoreplex’s Fraud Prevention Approach:
- Real-Time Detection: Scoreplex mitigates fraud within seconds by analyzing digital footprints, enabling immediate identification of fraudulent accounts and applications.
- Silent Checks: The platform conducts background evaluations without disrupting the user experience, ensuring a seamless onboarding process while strengthening fraud prevention measures.
- Comprehensive Data Integration: By aggregating data from over 300 sources, Scoreplex provides a holistic view of an applicant's digital identity, enhancing the accuracy of fraud detection and credit scoring.
- Advanced Risk Profiling: By utilizing AI, Scoreplex analyzes email, phone, and IP risk signals and contextual signals to assess the trustworthiness of applicants, identifying potential risks associated with synthetic identities or fraudulent activities.
- Global Coverage: Scoreplex ensures protection and compliance across international markets, offering unlimited global coverage to safeguard against fraud on a worldwide scale.
By integrating Scoreplex's digital footprint analysis into fraud prevention strategies, organizations can proactively detect and mitigate fraudulent activities, enhancing security and trust in their systems.




